A procedure to allow users to switch (su) to another user, using their own password instead of the “target” user password
I ran into the following scenario, which puzzled me for a while:
- Bob (unprivileged) needed to run a specific binary in a production environment, as Alice (privileged).
- We needed to find a way to accomplish this without needing Alice to share her password with Bob.
The problem we’re solving #
What we want here is to be able to:
- Bob needs to switch user (
su) to Alice, but using only his own password. Both on different groups.
Instead of the default option which is:
- Bob needs to switch to Alice (Who is on another group) by knowing Alice’s password.
The rest of this post explains exactly what I did to solve this problem.
Scenario #
We have 2 users in 2 different groups:
-
User 1: “user” (Unprivileged)
-
Group 1: “staff” (Unprivileged)
-
User 2: “Operator” (Privileged)
-
Group 2: “Operations” (Privileged)
The following was added in /etc/ssh/sshd_config file:
# Allow "staff" users to execute bash as "operator":
%staff ALL=(operator) /usr/bin/bash
NOTE: This lab scenario sets us to run Bash as a privileged user, which is generally not a good idea. In real scenarios we should instead assign the specific binary path we want, or command, making sure an unprivileged user cannot modify this same binary. We’re not aiming at giving an unprivileged user more privileges; we’re aiming at giving an unprivileged user one capability only a privileged user has.
The following means:
- “Staff” users can execute /bin/bash as user “operator”

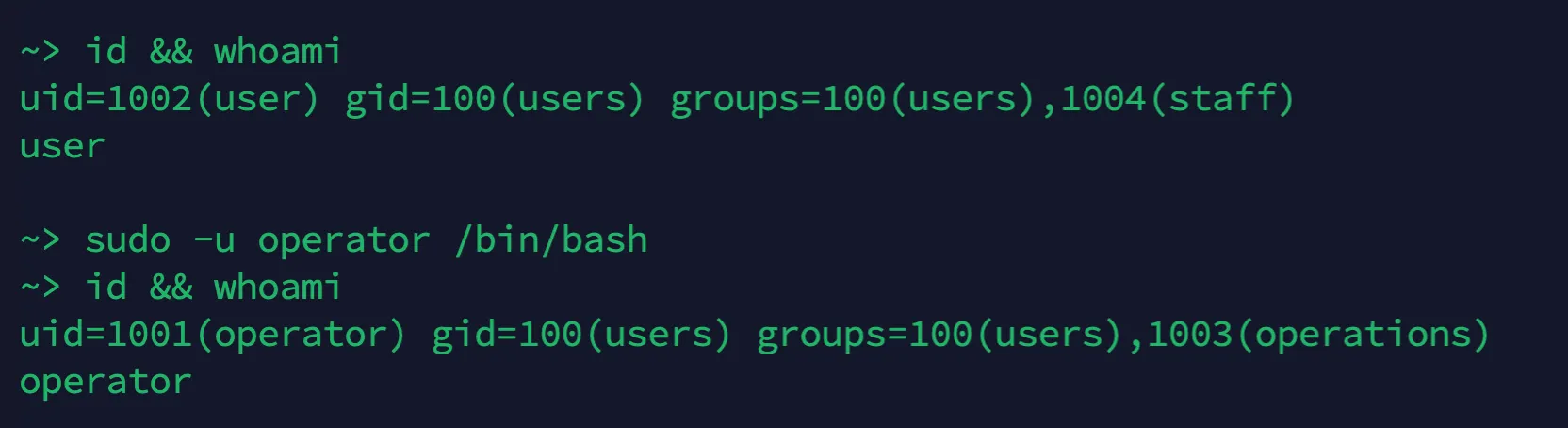
Before & after switching users #
Successfully switching user to “operator” without needing to be in that group, or knowing operator’s password
[!WARNING] As always, threat model, threat model, threat model.
